How did attackers drain $42M from @GMX_IO?
Through cross-contract reentrancy that bypassed every safety check.
We reproduced the attack using @WakeFramework.
Let's break it down ↓
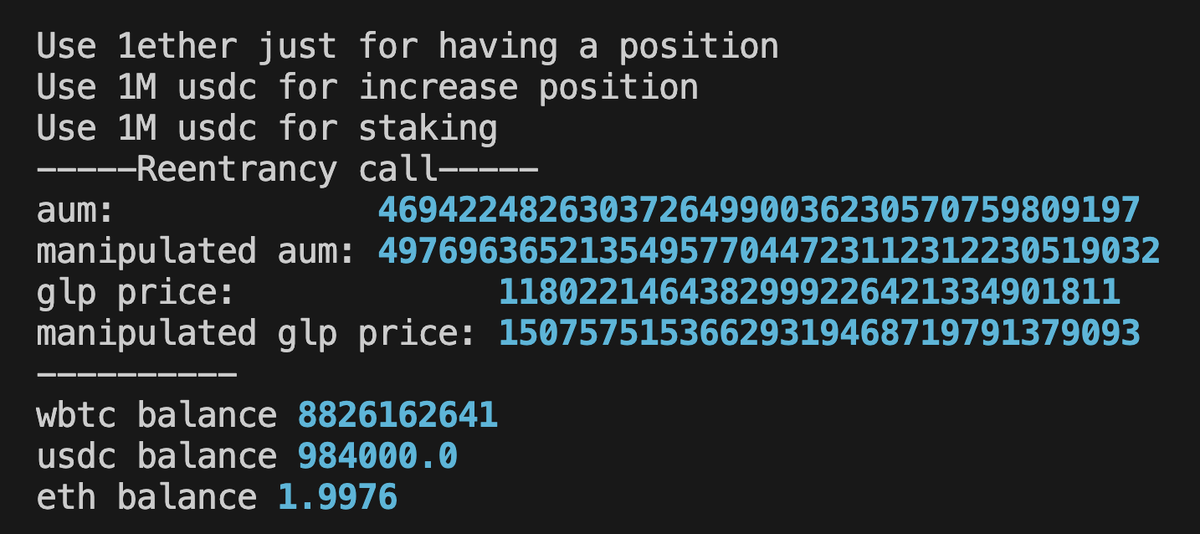
2/ Each GMX contract had reentrancy guards. The attack succeeded anyway. How?
The exploit occurred AFTER one contract's guard had already exited, creating a window to manipulate GLP token prices.
3/ The attack exploited fragmented data responsibility:
• Vault handles positions, ShortsTracker tracks prices
• Attacker re-enters after reentrancy guard resets
• Bypasses ShortsTracker update → inflates GLP price
• Drains value at manipulated prices
4/ Read the detailed analysis and reproduce the scenario. Full walkthrough and forked environment available.
Understanding these attacks is the first step to preventing them in your project.
6.37K
24
The content on this page is provided by third parties. Unless otherwise stated, OKX is not the author of the cited article(s) and does not claim any copyright in the materials. The content is provided for informational purposes only and does not represent the views of OKX. It is not intended to be an endorsement of any kind and should not be considered investment advice or a solicitation to buy or sell digital assets. To the extent generative AI is utilized to provide summaries or other information, such AI generated content may be inaccurate or inconsistent. Please read the linked article for more details and information. OKX is not responsible for content hosted on third party sites. Digital asset holdings, including stablecoins and NFTs, involve a high degree of risk and can fluctuate greatly. You should carefully consider whether trading or holding digital assets is suitable for you in light of your financial condition.

