Beosin Blockbuster | Web3 blockchain security landscape analysis in the first half of 2025
*This report is jointly produced by Beosin and Footprint Analytics
1. Overview of the Web3 blockchain security landscape in the first half of 2025
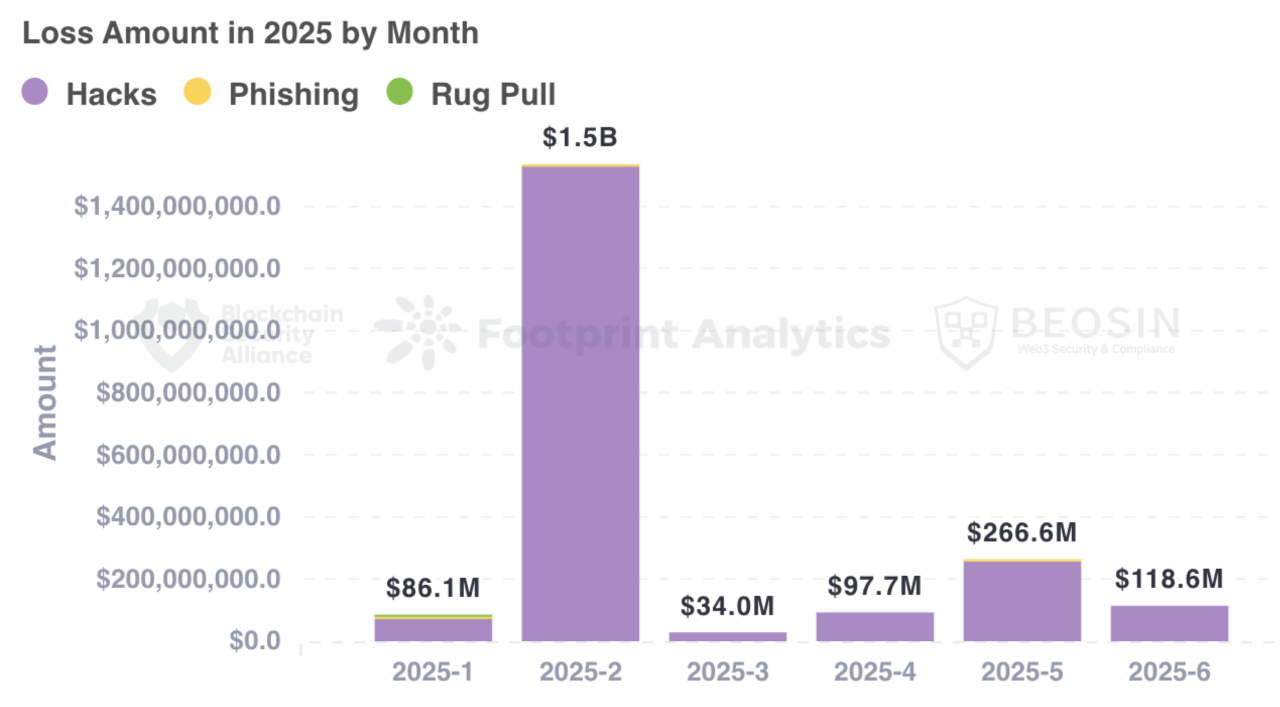
According to Beosin Alert, the total loss caused by hacking, phishing scams and Rug Pull in the Web3 field in the first half of 2025 will be about $2.138 billion. Among them, there were 90 major attacks, with a total loss of about $2.093 billion; Rug Pull's total losses amounted to approximately $3.2 million; The total loss of phishing scams was about $41.38 million.
From the perspective of the types of projects attacked, exchanges have become the type of projects with the highest amount of losses. The six attacks on the exchange platform caused a total of more than $1.591 billion in damages, accounting for 74.4% of all attack losses.
In terms of the amount of losses of each chain, Ethereum is still the chain with the highest loss...
