Sui price
in USDCheck your spelling or try another.


About Sui
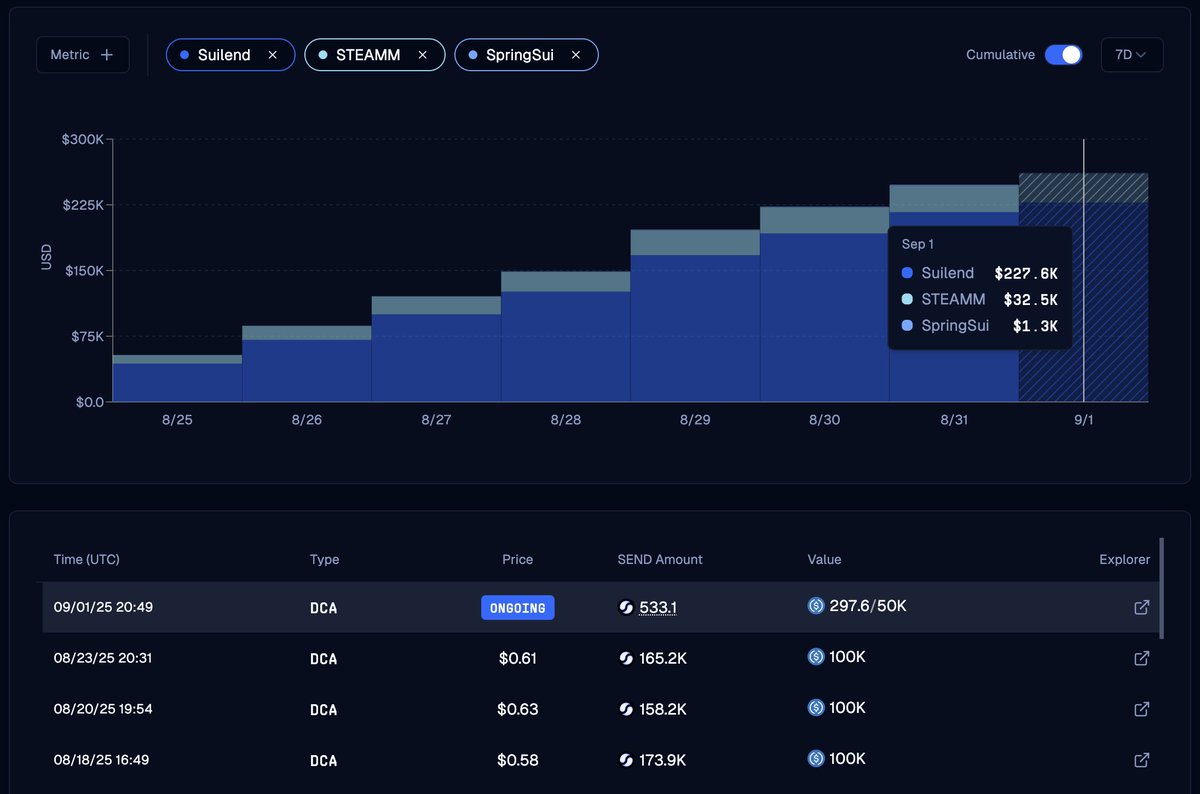
Sui’s price performance
Sui in the news

Stellar (XLM) was also among the underperformers, declining 2.5%.

Grayscale is offering accredited investors direct exposure to DEEP and WAL, the native tokens of Sui’s DeepBook and Walrus protocols

SUI slid to $3.69 after failing to break resistance near $3.98, with open interest dropping 15% and funding rates plunging from July highs.

Sygnum and Amina banks have added SUI trading, custody and lending products for professional investors.

Sygnum is expanding regulated Sui blockchain access for institutional clients with custody and trading, and plans to add staking and collateral-backed loans later this year.

Polygon (POL) joined Sui (SUI) as a top performer, rising 6.2% from Wednesday.
Sui on socials

Guides

Sui on OKX Learn

Sui FAQ
Dive deeper into Sui
Disclaimer
OKX does not provide investment or asset recommendations. You should carefully consider whether trading or holding digital assets is suitable for you in light of your financial condition. Please consult your legal/tax/investment professional for questions about your specific circumstances. For further details, please refer to our Terms of Use and Risk Warning. By using the third-party website ("TPW"), you accept that any use of the TPW will be subject to and governed by the terms of the TPW. Unless expressly stated in writing, OKX and its affiliates (“OKX”) are not in any way associated with the owner or operator of the TPW. You agree that OKX is not responsible or liable for any loss, damage and any other consequences arising from your use of the TPW. Please be aware that using a TPW may result in a loss or diminution of your assets. Product may not be available in all jurisdictions.